In the realm of data management, ensuring the backups of the SKED database is paramount for maintaining data integrity and safeguarding critical information. This comprehensive guide delves into the essential strategies, techniques, and best practices for securing your SKED database backups, providing a roadmap for reliable and efficient data protection.
Ensuring the Backups of the Sked Database
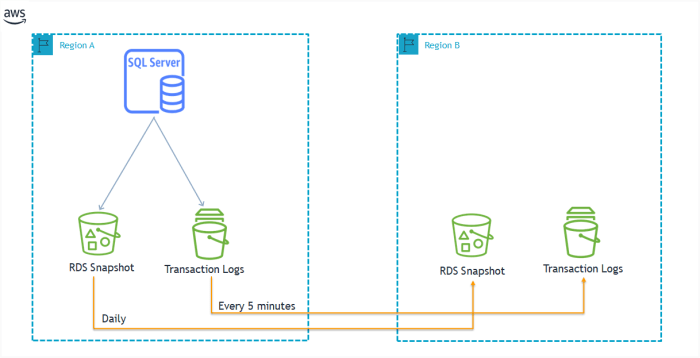
The Sked database contains critical information that is essential for the smooth operation of the business. It is therefore imperative to have a comprehensive backup strategy in place to ensure that the data is protected in the event of a hardware failure, software corruption, or human error.
Database Backup Strategy

A comprehensive backup strategy should include the following elements:
- Full backups:A full backup creates a complete copy of the entire database, including all data, indexes, and other metadata.
- Incremental backups:An incremental backup only backs up the data that has changed since the last full or incremental backup.
- Differential backups:A differential backup backs up all the data that has changed since the last full backup.
The frequency of backups and the retention period for backup files should be determined based on the criticality of the data and the recovery point objective (RPO) and recovery time objective (RTO) of the business.
Backup Verification and Validation
It is essential to verify and validate backups regularly to ensure that they are complete and can be restored successfully.
Backup verification involves checking the integrity of the backup file, while backup validation involves restoring the backup to a test environment to ensure that the data is accessible and usable.
Disaster recovery testing is a critical component of backup verification and validation. Disaster recovery testing involves simulating a disaster scenario and attempting to restore the database from a backup. This testing helps to ensure that the backup and recovery processes are working as expected.
Automation and Monitoring
Automating backup processes can help to ensure that backups are performed regularly and consistently.
Backup schedules can be set up to run automatically at a specified time and frequency. Backup monitoring can be used to track the status of backups and to alert administrators to any errors or failures.
Data Security and Encryption, Ensuring the backups of the sked database
Backups should be encrypted to protect them from unauthorized access. Encryption can be implemented using a variety of methods, including symmetric encryption, asymmetric encryption, and hashing.
The encryption key should be stored securely and should not be shared with anyone who does not need to access the backups.
Backup Storage and Management
Backups can be stored on a variety of media, including local hard drives, network-attached storage (NAS) devices, and cloud storage services.
The choice of storage media will depend on the size of the backups, the frequency of backups, and the security requirements of the business.
Backup storage should be managed carefully to ensure that backups are organized and easy to find and restore.
Compliance and Regulatory Requirements
Many industries have regulations and compliance standards that require businesses to maintain regular backups of their data.
Businesses should be aware of the compliance requirements that apply to them and should ensure that their backup strategy meets those requirements.
Best Practices and Case Studies
There are a number of best practices that businesses can follow to ensure reliable backups:
- Use a combination of full, incremental, and differential backups.
- Verify and validate backups regularly.
- Automate backup processes.
- Encrypt backups.
- Store backups on a variety of media.
- Manage backup storage carefully.
- Be aware of compliance requirements.
There are a number of case studies that demonstrate the benefits of implementing a reliable backup strategy.
For example, one company was able to recover from a major hardware failure within hours by restoring their database from a backup. Another company was able to avoid a costly data breach by encrypting their backups.
Essential FAQs: Ensuring The Backups Of The Sked Database
How often should I back up my SKED database?
The frequency of backups depends on the criticality of the data and the rate at which it changes. Daily or weekly backups are recommended for most databases.
What types of backup methods are available?
There are three main types of backup methods: full, incremental, and differential. Full backups capture the entire database, while incremental backups only capture changes since the last full or incremental backup, and differential backups capture changes since the last full backup.
How can I encrypt my SKED database backups?
Encryption protects your backups from unauthorized access. Common encryption methods include AES-256 and SSL/TLS.